Risk mitigation is a strategy to prepare for and lessen the effects of threats faced by a data center. Comparable to risk reduction, risk mitigation takes steps to reduce the negative effects of threats and disasters on business continuity (BC). Threats that might put a business at risk include cyberattacks, weather events and other causes of physical or virtual damage to a data center.
Risk mitigation planning is the process of developing options and actions to enhance opportunities and reduce threats to project objectives. Risk mitigation implementation is the process of executing risk mitigation actions. Risk mitigation progress monitoring includes tracking identified risks, identifying new risks, and evaluating risk process effectiveness throughout the project.
Risk Mitigation Strategies
General guidelines for applying risk mitigation handling options are shown in Figure 2. These options are based on the assessed combination of the probability of occurrence and severity of the consequence for an identified risk. These guidelines are appropriate for many, but not all, projects and programs.
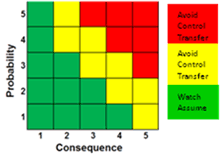
Figure 2. Risk Mitigation Handling Options
Risk mitigation handling options include:
- Assume/Accept: Acknowledge the existence of a particular risk, and make a deliberate decision to accept it without engaging in special efforts to control it. Approval of project or program leaders is required.
- Avoid: Adjust program requirements or constraints to eliminate or reduce the risk. This adjustment could be accommodated by a change in funding, schedule, or technical requirements.
- Control: Implement actions to minimize the impact or likelihood of the risk.
- Transfer: Reassign organizational accountability, responsibility, and authority to another stakeholder willing to accept the risk.
- Watch/Monitor: Monitor the environment for changes that affect the nature and/or the impact of the risk.
Each of these options requires developing a plan that is implemented and monitored for effectiveness. More information on handling options is discussed under best practices and lessons learned below.
From a systems engineering perspective, common methods of risk reduction or mitigation with identified program risks include the following, listed in order of increasing seriousness of the risk:
- Intensified technical and management reviews of the engineering process
- Special oversight of designated component engineering
- Special analysis and testing of critical design items
- Rapid prototyping and test feedback
- Consideration of relieving critical design requirements
- Initiation of fallback parallel developments
When determining the method for risk mitigation, the MITRE SE can help the customer assess the performance, schedule, and cost impacts of one mitigation strategy over another. For something like “parallel” development mitigation, MITRE SEs could help the government determine whether the cost could more than double, while time might not be extended by much (e.g., double the cost for parallel effort, but also added cost for additional program office and user engagement). For conducting rapid prototyping or changing operational requirements, MITRE SEs can use knowledge in creating prototypes and using prototyping and experimenting for projecting the cost and time to conduct a prototype to help mitigate particular risks (e.g., requirements). Implementing more engineering reviews and special oversight and testing may require changes to contractual agreements. MITRE systems engineers can help the government assess these (schedule and cost) by helping determine the basis of estimates for additional contractor efforts and providing a reality check for these estimates. MITRE’s CASA [Center for Acquisition and Systems Analysis] and the CCG [Center for Connected Government] Investment Management practice department have experience and a knowledge base in many development activities across a wide spectrum of methods and can help with realistic assessments of mitigation alternatives.
Types of Risk Mitigation
-
Risk Acceptance
Risk acceptance does not reduce any effects however it is still considered a strategy. This strategy is a common option when the cost of other risk management options such as avoidance or limitation may outweigh the cost of the risk itself. A company that doesn’t want to spend a lot of money on avoiding risks that do not have a high possibility of occurring will use the risk acceptance strategy.
-
Risk Avoidance
Risk avoidance is the opposite of risk acceptance. It is the action that avoids any exposure to the risk whatsoever. It’s important to note that risk avoidance is usually the most expensive of all risk mitigation options.
-
Risk Limitation
Risk limitation is the most common risk management strategy used by businesses. This strategy limits a company’s exposure by taking some action. It is a strategy employing a bit of risk acceptance along with a bit of risk avoidance or an average of both. An example of risk limitation would be a company accepting that a disk drive may fail and avoiding a long period of failure by having backups.
-
Risk Transference
Risk transference is the involvement of handing risk off to a willing third party. For example, numerous companies outsource certain operations such as customer service, payroll services, etc. This can be beneficial for a company if a transferred risk is not a core competency of that company. It can also be used so a company can focus more on their core competencies.
So how can I be a leader in Business Continuity Management (BCM) Governance, Risk and Compliance (GRC) and balance my risks and opportunities?
All of these four risk mitgiation strategies require montioring. Vigilence is needed so that you can recognize and interrperet changes to the impact of that risk.