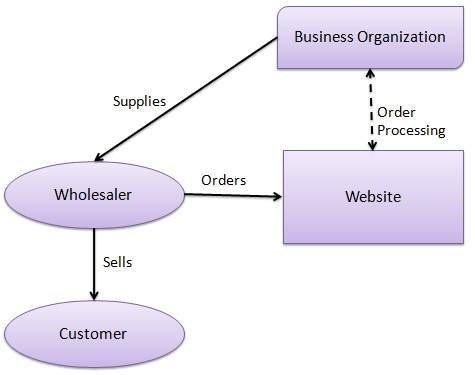
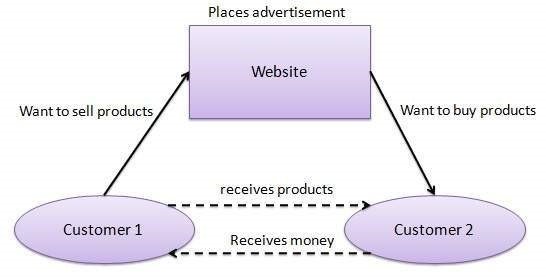
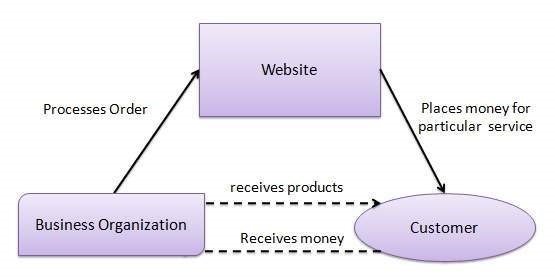
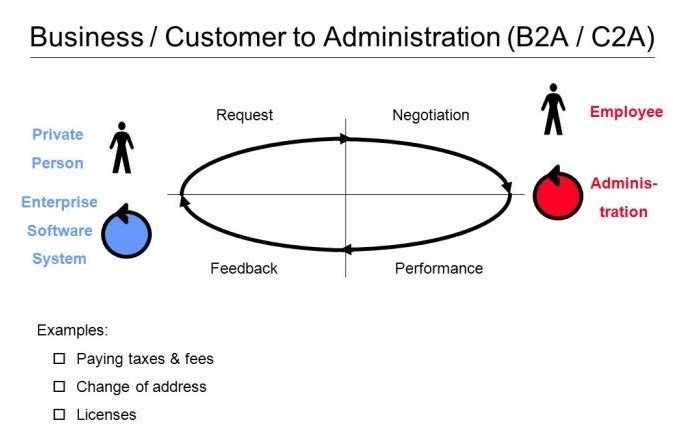
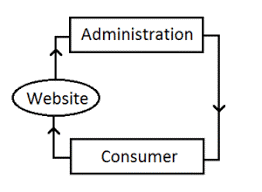
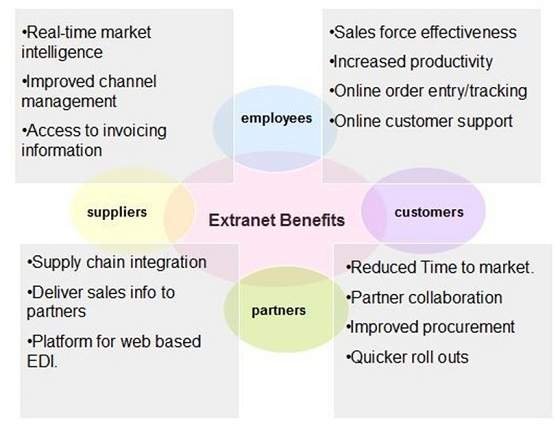
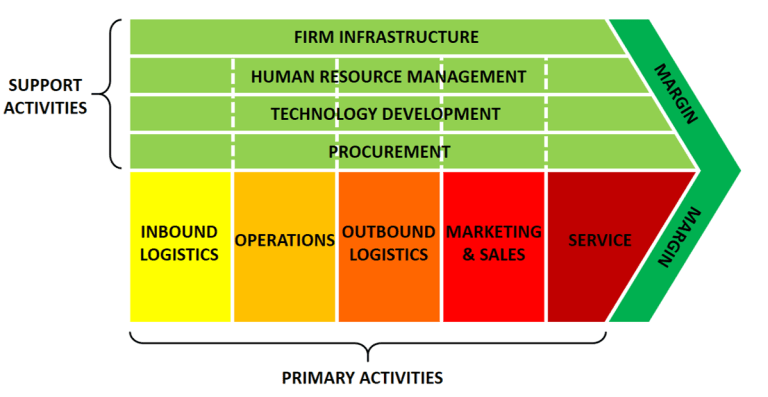
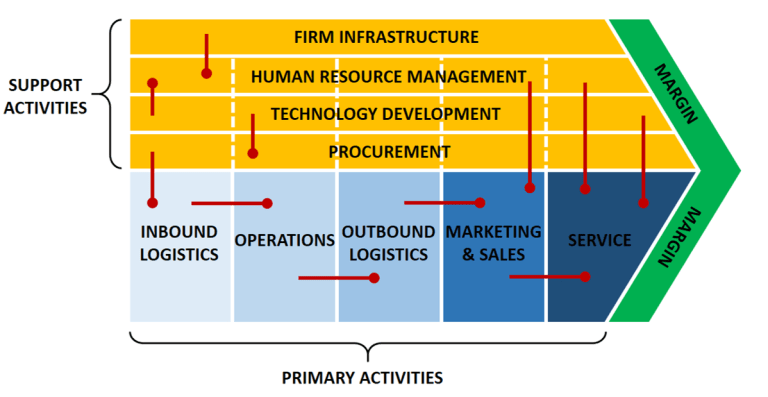
The Internet is a vast network of interconnected computers and other devices spanning the globe. It facilitates the exchange of data and information through a system of interconnected networks using standardized communication protocols. This network infrastructure enables a myriad of services, including email, instant messaging, file sharing, and access to the World Wide Web.
The Internet’s origins can be traced back to the late 1960s with the development of ARPANET, a project funded by the U.S. Department of Defense’s Advanced Research Projects Agency (ARPA). ARPANET was designed to create a decentralized communication network capable of withstanding partial outages, making it more resilient in the event of a nuclear attack.
As ARPANET expanded, other networks emerged, eventually forming the foundation of the modern Internet. In the 1980s, the development of the TCP/IP protocol suite standardized communication protocols, allowing diverse computer networks to interconnect seamlessly. This laid the groundwork for the global network we know today.
The Internet operates on a decentralized architecture, with no single point of control. Instead, it relies on a distributed system of interconnected routers, servers, and other networking devices to transmit data packets across vast distances. This decentralized nature contributes to the Internet’s robustness and resilience, as there is no single point of failure that could bring down the entire network.
The World Wide Web: A Network of Information
The World Wide Web, often referred to as the Web, is a subset of the Internet that consists of interconnected web pages and resources accessible via the Internet. It was invented by Sir Tim Berners-Lee, a British computer scientist, in the late 1980s while working at CERN, the European Organization for Nuclear Research.
Berners-Lee’s vision was to create a system for sharing and accessing information across different computer systems. He developed the foundational technologies that power the Web, including the Hypertext Transfer Protocol (HTTP) for transferring web resources, Uniform Resource Locators (URLs) for identifying web resources, and Hypertext Markup Language (HTML) for structuring web documents.
The Web revolutionized the way information is organized and accessed, providing a user-friendly interface for navigating a vast repository of digital content. Web pages are interconnected through hyperlinks, allowing users to navigate between different resources with ease. This interconnectedness forms the basis of the Web’s “hypertext” structure, where text, images, and other media are linked together in a non-linear fashion.
Key Components of the World Wide Web
Web browsers are software applications that allow users to access and navigate the World Wide Web. Popular web browsers include Google Chrome, Mozilla Firefox, Apple Safari, and Microsoft Edge. Browsers interpret HTML documents and render them as visually appealing web pages for users to interact with.
Web servers are computer systems that store and serve web content to clients upon request. When a user requests a web page, their browser sends a request to the appropriate web server, which then retrieves the requested content and sends it back to the client for display. Common web server software includes Apache HTTP Server, Nginx, and Microsoft Internet Information Services (IIS).
HTML is the standard markup language used to create web pages. It provides a set of tags that define the structure and content of a web document, including headings, paragraphs, images, links, and multimedia elements. Web browsers interpret HTML documents and render them as visually appealing web pages for users to interact with.
URLs are web addresses that identify the location of web resources on the Internet. They consist of several components, including the protocol (e.g., http:// or https://), the domain name (e.g., example.com), and the path to the specific resource (e.g., /page1.html). URLs enable users to access web pages and other resources using a standardized addressing scheme.
HTTP is the protocol used for transferring hypertext documents on the World Wide Web. It defines how web browsers and servers communicate with each other to request and transmit web resources. HTTP operates as a stateless protocol, meaning that each request from the client is processed independently, without any knowledge of previous interactions.
Hyperlinks are clickable elements embedded in web pages that allow users to navigate between different resources on the Web. They are typically displayed as text or images with an underlying URL. Clicking on a hyperlink redirects the user to the linked resource, whether it’s another web page, a multimedia file, or a downloadable document.
Evolution of the World Wide Web
Since its inception, the World Wide Web has undergone significant evolution, driven by technological advancements and changing user needs.
-
Web 1.0 (The Static Web):
The early days of the Web were characterized by static web pages containing primarily text and images. Content was created and published by a relatively small number of individuals and organizations, and user interaction was limited to browsing and consuming information.
-
Web 2.0 (The Social Web):
The emergence of Web 2.0 in the early 2000s marked a shift towards dynamic, interactive web experiences. This era saw the rise of social media platforms, user-generated content, and collaborative online communities. Web 2.0 technologies empowered users to create, share, and interact with content in new ways, blurring the lines between consumers and producers of information.
-
Web 3.0 (The Semantic Web):
Web 3.0, also known as the Semantic Web, is an ongoing evolution of the Web towards a more intelligent, interconnected network of data. It aims to make web content more machine-readable and interpretable by creating standardized formats for representing and linking data. Semantic technologies such as RDF (Resource Description Framework) and SPARQL (SPARQL Protocol and RDF Query Language) enable machines to understand the meaning and context of web content, paving the way for more sophisticated applications such as natural language processing, knowledge graphs, and personalized recommendations.
Challenges and Opportunities
While the Internet and the World Wide Web have revolutionized the way we communicate, collaborate, and access information, they also present various challenges and opportunities:
-
Privacy and Security:
The pervasive nature of the Internet raises concerns about privacy and security, as sensitive information can be intercepted, accessed, or exploited by malicious actors. Ensuring the confidentiality, integrity, and availability of data is paramount to maintaining trust and confidence in online interactions.
-
Digital Divide:
The digital divide refers to the gap between those who have access to digital technologies and those who do not. Disparities in access to the Internet and digital literacy skills can exacerbate existing inequalities, limiting opportunities for socio-economic advancement and participation in the digital economy.
-
Information Overload:
The abundance of information available on the Web can lead to information overload, making it challenging for users to find relevant and reliable content amidst the noise. Tools and techniques for information retrieval, filtering, and curation are essential for managing information overload and extracting value from vast amounts of data.
-
Cybersecurity Threats:
The interconnected nature of the Internet exposes individuals, organizations, and critical infrastructure to various cybersecurity threats, including malware, phishing, ransomware, and distributed denial-of-service (DDoS) attacks. Implementing robust cybersecurity measures, such as encryption, authentication, and intrusion detection, is essential for mitigating these threats and safeguarding digital assets.
-
Ethical and Legal Implications:
The proliferation of digital technologies raises complex ethical and legal questions related to intellectual property rights, online privacy, freedom of expression, and algorithmic bias. Balancing innovation and regulation is crucial for ensuring that the Internet and the World Wide Web remain open, inclusive, and beneficial for society as a whole.
Like this:
Like Loading...