Customer-to-Customer (C2C) e-commerce, Characteristics, Types, Benefits, Challenges
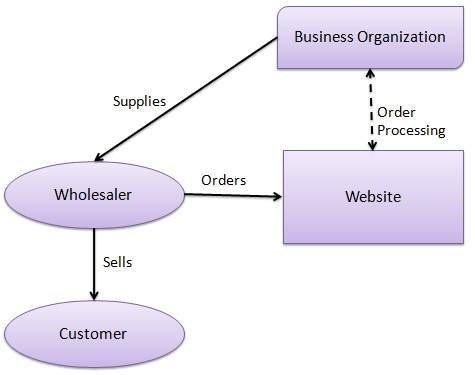
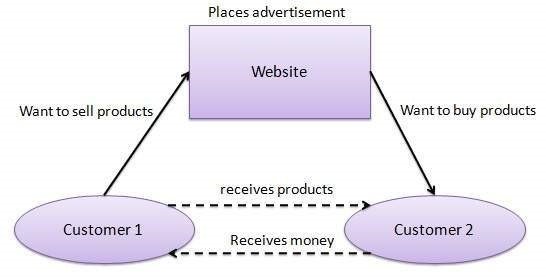
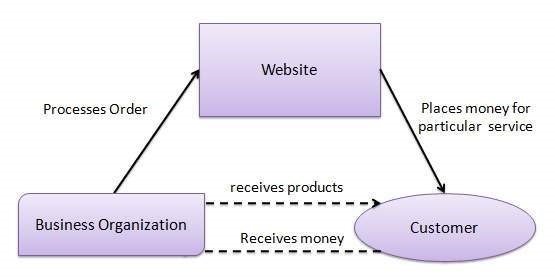
Customer-to-Customer (C2C) e-commerce refers to online transactions where individual consumers buy and sell goods or services directly to and from each other through digital platforms. These platforms act as intermediaries, facilitating the exchange of products or services between individuals, without the involvement of businesses as sellers. Examples of C2C e-commerce platforms include online marketplaces like eBay, Craigslist, and Facebook Marketplace, where individuals can list items for sale, negotiate prices, and complete transactions. C2C e-commerce enables individuals to monetize unused or unwanted items, find unique goods, and engage in peer-to-peer commerce, fostering a dynamic and decentralized marketplace driven by consumer-to-consumer interactions.
Characteristics of Customer-to-Customer (C2C) e-commerce:
-
Peer-to-Peer Transactions:
C2C e-commerce involves direct transactions between individual consumers, bypassing traditional business intermediaries.
-
Individual Sellers:
In C2C e-commerce, individuals act as both sellers and buyers, listing items for sale or auction and purchasing goods from other individuals.
-
Online Marketplaces:
C2C e-commerce platforms provide digital marketplaces where individuals can list items for sale, browse listings, and communicate with other users.
-
Variety of Products:
C2C platforms offer a wide range of products and services, including used goods, handmade items, collectibles, and unique or niche products.
-
User-Generated Content:
C2C e-commerce relies on user-generated content, including product listings, descriptions, images, and reviews, to facilitate transactions and build trust among users.
-
Informal Transactions:
Transactions in C2C e-commerce platforms often involve informal negotiations, haggling over prices, and flexible payment and delivery arrangements.
-
Community Engagement:
C2C platforms foster community engagement and interaction among users through features such as forums, messaging, and social sharing, enhancing the overall user experience.
-
Trust and Reputation:
Trust and reputation play a crucial role in C2C e-commerce, as buyers rely on seller ratings, reviews, and feedback to assess reliability and credibility before making purchases.
Types of Customer-to-Customer (C2C) e-commerce:
-
Online Classifieds:
Platforms like Craigslist and Gumtree allow individuals to list items for sale or trade in local or regional markets, facilitating C2C transactions.
-
Online Auctions:
Websites such as eBay enable individuals to auction off goods to the highest bidder, creating dynamic marketplaces for buying and selling a wide range of products.
-
Peer-to-Peer Rental:
C2C rental platforms like Airbnb and Turo enable individuals to rent out their properties, vehicles, or other assets to other consumers for short-term use.
-
Freelance Services:
Online platforms such as Upwork and Fiverr connect individuals seeking freelance work with those offering services such as graphic design, writing, programming, and digital marketing.
-
Peer-to-Peer Lending:
Peer-to-peer lending platforms like Prosper and Lending Club allow individuals to lend money directly to other individuals or businesses in exchange for interest payments.
-
Ticket Resale:
C2C ticket resale platforms like StubHub and Ticketmaster Resale enable individuals to buy and sell tickets for events such as concerts, sports games, and theater performances.
-
Swapping and Bartering:
Online communities and platforms facilitate C2C exchanges through swapping and bartering of goods and services without the use of money.
-
Social Commerce:
Social media platforms like Facebook Marketplace and Instagram enable individuals to buy and sell goods directly within their social networks, leveraging peer-to-peer connections for transactions.
Benefits of Customer-to-Customer (C2C) e-commerce:
-
Wide Product Selection:
C2C platforms offer a diverse range of products and services, including unique and niche items that may not be readily available through traditional retail channels.
-
Lower Prices:
Direct transactions between individuals often result in lower prices compared to buying from businesses, as sellers may offer used or second-hand items at discounted rates.
-
Opportunity for Income:
C2C e-commerce provides individuals with an opportunity to monetize unused or unwanted items by selling them to other consumers, generating additional income.
- Flexibility:
C2C platforms offer flexibility in terms of listing items for sale, setting prices, and negotiating with buyers, allowing individuals to control their selling process.
-
Community Engagement:
C2C e-commerce fosters community engagement and interaction among users, creating a sense of belonging and facilitating communication and collaboration.
-
Market Research:
Buyers can access valuable market insights and trends by browsing listings and observing buying behaviors on C2C platforms, helping them make informed purchasing decisions.
-
Environmental Benefits:
C2C e-commerce promotes sustainability by extending the lifespan of products through reuse and recycling, reducing waste and environmental impact.
- Empowerment:
C2C e-commerce empowers individuals to become entrepreneurs and build their own businesses, regardless of geographical location or traditional barriers to entry, fostering economic empowerment and entrepreneurship.
Challenges of Customer-to-Customer (C2C) e-commerce:
-
Trust and Security:
Establishing trust between buyers and sellers can be challenging in C2C transactions, as individuals may be concerned about fraud, scams, or receiving misrepresented goods.
-
Quality Control:
Maintaining product quality and consistency can be difficult in C2C e-commerce, as sellers may offer used or second-hand items with varying levels of condition and reliability.
-
Payment Risks:
C2C transactions may involve risks related to payment processing, including fraudulent transactions, payment disputes, and chargebacks, posing challenges for both buyers and sellers.
-
Logistics and Shipping:
Managing shipping and delivery logistics can be complex in C2C e-commerce, especially for individual sellers who may lack access to affordable shipping services or struggle with packaging and fulfillment.
-
Marketplace Competition:
C2C platforms often face intense competition from other online marketplaces and traditional retail channels, making it challenging for sellers to attract buyers and stand out in the crowded marketplace.
-
Regulatory Compliance:
C2C e-commerce platforms must comply with various regulations and legal requirements related to consumer protection, taxation, and online transactions, which can be complex and costly to navigate.
-
Customer Service:
Providing satisfactory customer service and support can be challenging in C2C transactions, as sellers may lack the resources or expertise to address buyer inquiries, complaints, or issues effectively.
-
Seller Reputation:
Building and maintaining a positive seller reputation is crucial in C2C e-commerce, as buyers rely on seller ratings, reviews, and feedback to assess credibility and trustworthiness, posing challenges for new or inexperienced sellers.