Traditionally, organizations have relied on policies to communicate high-level directives from the management. These documents, once issued, provide top down influence for everyone in the company from business units to departments to individual employees. Furthermore, these policies typically were developed at one time in the organization’s evolution to capture the current environment. One of the major challenges for an organization in this area is the continued growth and adaptation of the policies to mirror the transformation within the organization. The fastest area of growth and change within an organization is Information Systems. With the rapid development and push toward new technologies, organizations find themselves striving to maintain current technical environments with outdated policies. Secondly, with the emergence of new technology strategies such as Intranets and Extranets, security and the protection of informational assets has become paramount.
The first step is an enterprise-wide Information Systems Security Policy that is consistently enforced even as business needs change. Unfortunately, most companies have only bits and pieces of security scattered throughout the organization. These may make some departments or individuals feel safe, but they do little to protect the enterprise as a whole.
To address these needs, PricewaterhouseCoopers has designed a Security Knowledge Management system the Enterprise Security Architecture System (ESAS). The idea is to assist an organization in providing a key security infrastructure tool. Primarily ESAS is built on PPT methodology (People, Policy & Technology). Over the period PwC also went ahead mapping ESAS with COBIT methodology from ISACA and the guidelines given in ISO 17799.
PPT Methodology
PPT stands for People, Policy, & Technology. The security process is a mixture of these three elements. Each element depends in some manner on the other elements. Also, issues receive greater coverage when the elements are combined. The controls environment is greatly enhanced when these three elements work in concert. A simple drawing will suffice to illustrate this (see Figure 1). This drawing shows the basic elements and also the coverage areas.
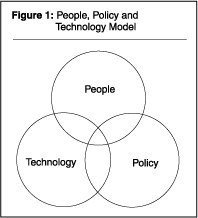
As you move toward the union of these elements, the controls environment increases there is greater coverage. Let’s understand these three elements individually.
People
This core element is the most important. The people element comprises the people and various roles and responsibilities within the organization. These are the people that are put in place to execute and support the process. A few key roles include senior management, security administrators, system and IT administrators, end users, and auditors.
Policy
This element comprises the security vision statement, security policy and standards, and the control documentation. This is basically the written security environment the bible that the security process will refer to for direction and guidance.
Technology
This element includes tools, methods, and mechanisms in place to support the process. These are core technologies the operating systems, the databases, the applications, the security tools embraced by the organization. The technology then is the enforcement, monitoring, and operational tool that will facilitate the process.
The concept is that each core element could be measured for effectiveness and coverage. Also, issues can be measured against the model to determine what controls coverage for that issue. The objective then is to move issues into the intersecting areas of the elements with the final objective of moving the issue into the middle area of greatest coverage. As risk issues are identified, each step to manage the risk will fall into one of the core elements of people, policy, or technology. If the issue is resolved with one of the elements, addressing one of the other elements can enhance this resolution. As the core elements are added to the controls environment and utilized in concert, the issue is then resolved on several fronts. The controls coverage is greater.
The PPT Model
The PPT Model can be illustrated with a few simple examples. Figure 2 shows the PPT Model with regards to Internet usage and misuse. Users are educated on the proper usage of the Internet. The controls environment relies solely on the user. An Internet usage policy is written to document proper use of the Internet and the consequences of misuse. The controls environment now is supported by two of the three core elements.

Filtering software is deployed on the firewall. Now the controls environment is covered by all three elements. Figure 3 demonstrates when an issue is covered only by two of the three elements. It also shows the consequence of a limited controls environment.
The Internet connection is protected by the deployment of a firewall. Core elements coverage = 1.
The firewall administrator receives specialized training and develops the skill set necessary to administer the firewall. Core elements coverage = 2.
The firewall administrator leaves the organization. The controls now rely back on just one element the technology.
How can the model be used to identify an alternative solution to Figure 3?
This is depicted in Figure 4.
The Internet connection is protected by the deployment of a firewall. Core elements coverage = 1.
The firewall administrator receives specialized training and develops the skill set necessary to administer the firewall. Core elements coverage = 2.
Firewall operating standards are written and controls are documented. Core elements coverage = 3.
The firewall administrator leaves the organization. The controls environment relies on two of the core elements. The controls, standards, and technology are documented so that the skill and knowledge does not completely leave the organization. Core elements coverage = 2.
From these examples, it is easy to see how the PPT model can simplify the analysis of a risk issue. If the issue is broken down into the three core elements, action items can be determined for each core element. In this manner, control coverage can be moved from one element to two, and ultimately to coverage by all of the elements.
The PPT model sounds like a very comfortable proposition but during actual implementation, CIO’s used to get lost in the framework. This is simplified by the ESAS tool.
The ESAS repository
ESAS is a Security Knowledge Management tool designed to bridge the gap between business and technology. It provides organizations with a centralized repository of security policies and technical control information. ESAS allows an organization to effectively communicate security policies and controls throughout the enterprise, and provide the key infrastructure for a successful Information Security program.

The major objectives of the ESAS are:
- Ensure consistency of organizational security objectives throughout operating units
- Allow business strategies and goals to drive Information Security
- Allow an organization to deal with the changes in both business initiatives and technology and manage the risk associated with change
- Provide a comprehensive set of security policies for the organization
- Provide a method to look at information and technical systems from a Risk perspective
- Provide the methods to implement security objectives effectively and efficiently at a technical level
ESAS is built on a unique security model/Framework (explained below) to provide flexibility in managing the information.
Understanding the Security Framework
PricewaterhouseCoopers’ Information Security Framework provides the overall model for developing comprehensive security programs. The framework illustrates an enterprise approach for security.

Key elements, also referred to as the “Four Pillars” to Information Security, include:
- Solid Senior Management Commitment
- An overall Security Vision and Strategy
- A comprehensive Training and Awareness Program
- A solid Information Security Management Structure including key skill sets and documented responsibilities
Within the four “pillars” of the program, several phases are included.
The first is the Decision Driver Phase, which contains factors determining the business drivers of security. These include Technology Strategy and Usage, Business Initiatives and Processes and Threats, Vulnerabi-lities and Risk. All these combine to form a unique “Security Profile” of the organization. The “profile” needs to be reflected in the Security Policies and Technical Controls.
The next facet of the Information Security Framework includes the design of the security environment also called the Design Phase. This is the stage where the organization documents its security policy, the control environment and deals with controls on the technology level. A key element in this process is not only the clear definition of security policy and technical control information, but also the “Security Model” of the enterprise. Information Classifications and Risk Assessment methods fall under this component. These processes allow the organization to manage risk appropriately and identify the risks and values of information assets.
The final facet of the Information Security Framework is the Implementation phase. This begins by documenting the Administrative and End-User guidelines and procedures. These guidelines must be succinct and flexible for the changing environment. Enforcement, Monitoring, and Recovery processes are then layered on for the operational support of the security program. These processes are “where the rubber hits the road”. All the benefits of the Security Program design and documentation is diminished if it is not put into effect on an operational day-to-day basis.